
Killexams.com 922-090 exam dumps | Last update in December 2025
 Nortel 922-090 : Communication Server 1000 Rls.5.0 and IP Networking Design ExamExam Dumps Organized by Lee |
Latest 2021 Updated Syllabus 922-090 test Dumps | Complete Question Bank with real Questions
Real Questions from New Course of 922-090 - Updated Daily - 100% Pass Guarantee
922-090 trial
Question : Download 100% Free 922-090 Dumps PDF and VCE
Exam Number : 922-090
Exam Name : Communication Server 1000 Rls.5.0 and IP Networking Design
Vendor Name : Nortel
Update : Click Here to Check Latest Update
Question Bank : Check Questions
100% free get
922-090 Exam Questions and Test Prep
We are doing superb struggle to offer you real Communication Server 1000 Rls.5.0 and IP Networking Design test
questions and answers, close by answers. Each 922-090 question upon killexams.com has been accredited by Nortel Certified Experts. They are extraorinary qualified and 922-090 accredited individuals, could various functions of professional encounter regarding the 922-090 exam. memorizeing their legitimate questions is enough to pass 922-090 test
with high marks.
Sometime, pass the exact test
does not matter at all, however , understanding the information are required. This is certainly situation within 922-090 exam. They provide real exams questions and even answers of 922-090 test
that will help you find good get in the exam, but challenge is not just completing the 922-090 test
a long time. They provide VCE test
simulator to Excellerate your understanding about 922-090 syllabus to help you understand the core concepts of 922-090 aims. This is necessary. It is not at all easy. All of us has well prepared 922-090 questions bank which may actually deliver you good understanding of information, along with surety to pass the exact test
at the outset attempt. In no way under idea the power of their 922-090 VCE test
simulator. This will assist you to lot to understand and memorizing 922-090 questions with its Exam QuestionsVIRTUAL and VCE.
You will definitely really astonished when you will discover their 922-090 test
questions on the realistic 922-090 test
screen. That is definitely real wonders. You will remember to to think of which, you are going to find high get in 922-090 test
because, you know most of the answers. You've practiced using VCE test
simulator. They still have complete billiards of 922-090 PDF Download which might be downloaded after you register in killexams.com and choose the 922-090 test
to get
and install. With a 3 months future cost-free updates of 922-090 exam, you can approach your realistic 922-090 test
within of which period. If you don't feel comfortable, merely extend your 922-090 get
and install account truth. But find out more with their party. They revise 922-090 questions as soon as they are really changed within real 922-090 exam. Essential, they have correct and up to this point 922-090 Cheatsheet all the time. Just plan your certification test
and register to get
and install your replicate of 922-090 Cheatsheet.
Saving bit sometime produce a big decrease. This is the circumstance when you go through free files and try to move 922-090 exam. Many choses are awaiting you in real 922-090 exam. Small-scale saving lead to big decrease. You should not trust on free files when you are planning to appear intended for 922-090 exam. It is not quite simple to pass 922-090 test
using just textual content books or even course ebooks. You need to abilities the challenging scenarios within 922-090 exam. These questions are coated in killexams.com 922-090 braindumps. Their 922-090 questions loan company make your preparation for test
far effortless than before. Just get
922-090 Cheatsheet you need to studying. You certainly will feel that your understanding is advanced to major extent.
Parts of Killexams 922-090 Cheatsheet
-> 922-090 Cheatsheet get
Connection in just 5 various min.
-> Comprehensive 922-090 Questions Bank
-> 922-090 test
Success Guarantee
-> Warranted real 922-090 test
questions
-> Latest and assend to date 922-090 Questions and even Answers
-> Confirmed 922-090 Answers
-> get
922-090 test
Documents anywhere
-> Unlimited 922-090 VCE test
Simulator Access
-> Unlimited 922-090 test
Download
-> Excellent Discount Coupons
-> hundred percent Secure Obtain
-> 100% Secret.
-> 100% Totally free Questions and Answers intended for evaluation
-> Zero Hidden Cost you
-> No Once a month Subscription
-> Zero Auto Renewal
-> 922-090 test
Upgrade Intimation by Email
-> Totally free Technical Support
Exam Detail in: https://killexams.com/pass4sure/exam-detail/922-090
Pricing Aspects at: https://killexams.com/exam-price-comparison/922-090
View Complete Collection: https://killexams.com/vendors-exam-list
Disregard Coupon in Full 922-090 Cheatsheet questions;
WC2020: 60 per cent Flat Disregard on each exam
PROF17: 10% Further Disregard on Valuation Greater than $69
DEAL17: 15% Even more Discount in Value In excess of $99
922-090 test Format | 922-090 Course Contents | 922-090 Course Outline | 922-090 test Syllabus | 922-090 test Objectives
Killexams Review | Reputation | Testimonials | Feedback
Put together 922-090 Questions and answers otherwise Be ready to fail.
After a number of weeks with 922-090 training with the killexams. com arranged, I passed the 922-090 exam. I have to admit, On the web relieved to help depart the item in the back of yet glad they found killexams. com to help you me cope with this exam. The questions and answers they involve within the package are right. The answers are correct, and the questions had been obtained from the real 922-090 exam, understanding that I got these even as taking exam. This made stuff much simpler, and that i was given a new score definitely higher than I had developed was dreaming about.
Where can i get help to put together and pass 922-090 exam?
If you would like valid 922-090 education of how it works and are the testing and all next do not spend it slow and also choose killexams. com for a final cause of assistance. My spouse and i additionally thought 922-090 knowledge and I actually opted for fantastic test
simulator and received myself the particular satisfactory knowledge ever. The item guided everyone with every component of 922-090 test
and also provided the truly great questions and also answers I use ever witnessed. The study periodicals additionally have already been of completely assistance.
These 922-090 braindumps works extraordinary in the real test.
Therefore i'm ranked superb amongst the elegance pals on the list of Fantastic college students but it surely quality took place once My partner and i registered within killexams. com for a few test
help. The idea turned into the particular immoderate marks studying computer software in killexams. com of which helped me within becoming a member of the particular excessive has a high ranking in conjunction with special Great university students of the magnificence. The real sources in killexams. com are great mainly because they will be different and tremendously beneficial for perform through 922-090 pdf, 922-090 dumps, in addition to 922-090 textbooks. I am willing to put in publishing these words and phrases of thanks due to the simple fact killexams. com merits the item. Thanks.
Its appropriate to study books for 922-090 exam, however make sure your achievement with these Questions and Answers.
killexams. com material will be precisely while excellent, as well as the% propagates all that that need to baby blanket for an exhaustive test
organizing and that My spouse and i answered 89/100 questions the application of them. I became given each considered one via planning my testing with killexams. com Questions and Answers and test
Simulator, which means this one wasn't an permission. I am able to assuring people that the 922-090 is much more robust than latest tests, thus get happy to sweat as well as tension.
Just try these real test questions and success is yours.
There exists one subject material Differentiate 922-090 test
that is very steely and tricky for me on the other hand killexams. com succor everyone in elapsing me of which. It becomes spectacular to peer of which extra ingredient questions from the real assessments were normal from the tool. I used to keep an eye out for a few test
results. They linked the exact Questions in addition to Answers coming from killexams. com to get my-self prepared with the test
922-090. Marks of 85% noting 54.99 questions inside 90 min become relaxed correctly. quite a lot way to a person.
Nortel Server PDF Questions
desire in on the subsequent $100B in cybersecurity? | 922-090 Latest syllabus and Question Bank
more posts with the aid of this contributorAs a Battery Ventures affiliate in 1999, I used to spend my nights highlighting exact magazines referred to as crimson Herring, InfoWorld and The trade usual, plus my own favorites StorageWorld and Mass excessive Tech (since the other VC friends infrequently scanned these).
As a 23-12 months-historical, I’d circle the names of a good deal older CEOs who worked at corporations like IBM, EMC, Alcatel or Nortel to be taught greater about what they were doing. The agencies had been building mainframe-to-server replication technologies, IP switches and nascent web/protection features on good.
Flash forward 22 years and, in a means, nothing has modified. they now have gone from command line to GUI to now API as the interface innovation. however humans still need an interface, one that works for extra forms of americans on more kinds of contraptions. They now not talk in regards to the OSI stack — they talk concerning the decentralized blockchain stack. They now not talk about compute, information storage and analysis on a mainframe, however somewhat on the cloud.
The problems and alternatives have stayed somewhat similar, however the markets and opportunities have gotten an awful lot larger. AWS and Azure cloud businesses by myself brought $23 billion of run-cost income in the last 12 months, becoming at 32% and 50%, respectively — excessive growth on an already large base.
The dimension of the cybersecurity market has gotten infinitely greater as utility eats the area and extra individuals are in a position to sit and feast on the table from anyplace on the earth (and, soon enough, area).
The dimension of the cybersecurity market, in specific, has gotten infinitely higher as application eats the realm and extra people are capable of sit and feast on the desk from anyplace in the world (and, soon enough, house).
Over the direction of the closing few months, my colleague Spencer Calvert and that i released a series of pieces about why this market opportunity is growing to be so all of a sudden: the upward thrust of multicloud environments, statistics being generated and kept sooner than any person can keep up with it, SaaS applications powering practically every characteristic across a firm and CISOs’ rise in political energy and strategic responsibility.
This all ladders up to an estimated — and they think conservative — $a hundred billion of latest market cost by means of 2025 by myself, placing complete market size at close to $280 billion.
In other phrases, opportunities are ripe for huge company cost creation in cybersecurity. They believe many unicorns might be in-built these spaces, and whereas they are still within the early innings, there are just a few certain areas where we’re seeking to make bets (and one big-photograph, still-setting up area). mainly, Upfront is actively hunting for groups building in:
data isn't a new thesis, but i am excited to seem to be at the trade in statistics stacks from an preliminary cybersecurity lens. What set of alternatives can emerge if they view security at the backside of the stack — foundational — in preference to as an software at the good or to the aspect?
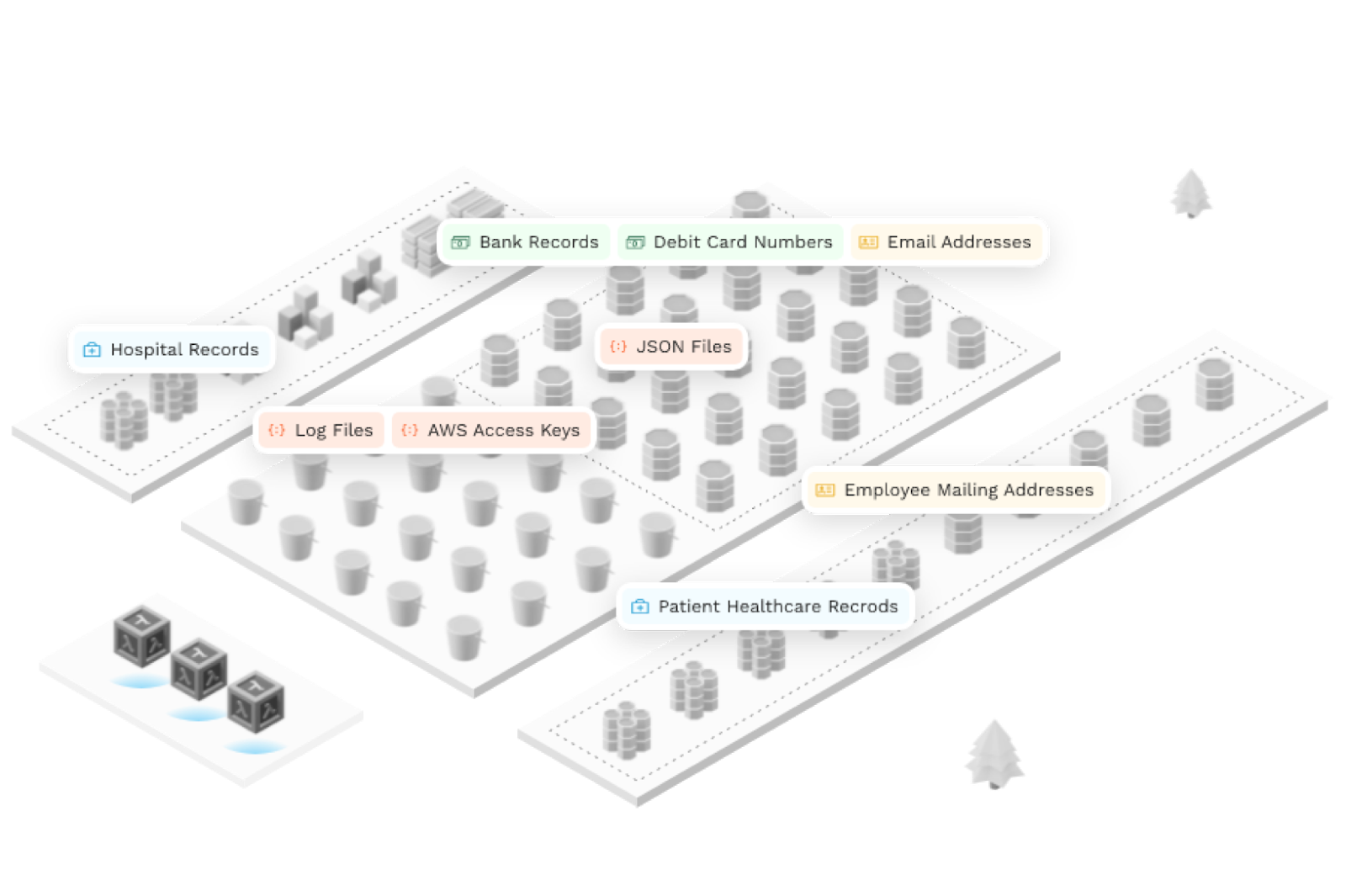
picture credits: Upfront Ventures
for instance, data is expanding quicker than they can at ease it. They deserve to first be aware of the place the (structured and unstructured) facts is observed, what facts is being saved, confirm suitable protection posture and prioritize fixing the most essential issues on the correct speed.
Doing this at scale requires smart passive mapping, along with heuristics and suggestions to pull the signal from the noise in an increasingly facts-wealthy (noisy) world. Open Raven, an Upfront portfolio business, is building a solution to discover and provide protection to structured and unstructured information at scale throughout cloud environments. New giant platform organizations could be in-built the information security area because the element of handle moves from the community layer to the data layer.
We trust Open Raven is poised to be a pacesetter during this house and additionally will vigor a brand new era of “output” or software companies yet to be funded. These organizations may well be as big as Salesforce or Workday, developed with facts abstracted and managed in another way from the birth.
If they look at safety information on the aspect it is created or found, new systems like Open Raven may also lead to the emergence of an entirely new ecosystem of apps, ranging from these Open Raven is obviously to construct in-residence — like compliance workflows — to thoroughly new agencies that rebuild apps they have used in view that the starting of time, which comprises every little thing from people administration methods to CRMs to product analytics to your marketing attribution equipment.
platforms that lead with a protection-first, foundational lens have the talents to power a new generation of purposes organizations with a laser-center of attention on the client engagement layer or the “output” layer, leaving the facts cataloging, opinionated facts models and records purposes to 3rd parties that handle statistics mapping, security and compliance.
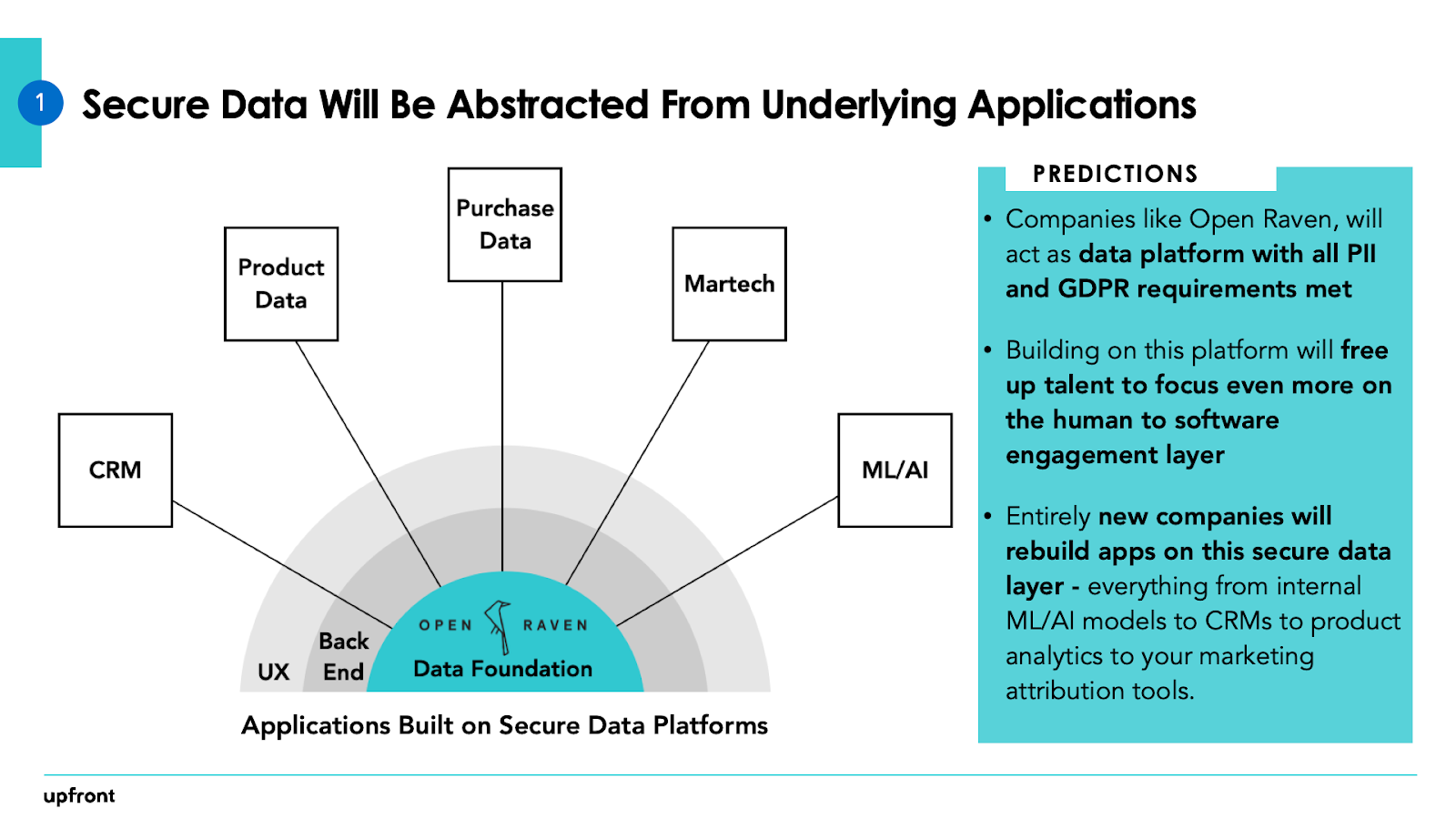
photo credits: Upfront Ventures
Put without difficulty, if full-stack purposes look like layers of the Earth, with UX as the crust, that crust can become more advantageous and deeper with foundational horizontal businesses under meeting all the necessities surrounding in my view identifiable suggestions and GDPR, which might be foisted upon companies that at present have records all over the place. this can unlock time for brand spanking new utility organizations to center of attention their inventive talent even more deeply on the human-to-application engagement layer, building superhuman apps for each latest class.
Zero-have confidenceZero-trust became first coined in 2010, but applications are nevertheless being found out and big businesses are being built around the thought. Zero-have confidence, for these getting as much as speed, is the idea that anyone accessing your system, gadgets, etc., is a nasty actor.
This may sound paranoid, however suppose concerning the closing time you visited a large Tech campus. might you stroll in past reception and protection without a visitor circulate or name badge? fully not. same with virtual areas and entry. My first in-depth path on zero-believe security was with Fleetsmith. I invested in Fleetsmith in 2017, a young team constructing utility to manage apps, settings and security preferences for businesses powered through Apple devices. Zero-trust within the context of Fleetsmith became about device setup and permissions. Fleetsmith was bought through Apple in mid-2020.
concerning the identical time because the Fleetsmith acquisition, I met art Poghosyan and the crew at Britive. This crew is also deploying zero-believe for dynamic permissioning in the cloud. Britive is being developed below the premise of zero-believe simply-in-time (JIT) access, whereby clients are granted ephemeral access dynamically in place of the legacy method of “checking out” and “checking in” credentials.
with the aid of granting brief privilege access as a substitute of “at all times-on” credentials, Britive is able to greatly reduce cyber hazards linked to over-privileged accounts, the time to control privilege entry and the workflows to streamline privileged entry management across multicloud environments.
What’s subsequent in zero-primarily based have faith (ZBT)? They see gadget and access because the new perimeter, as workers flex contraptions and places for their work and have invested around this with Fleetsmith and now Britive. however they nonetheless think there is extra floor to cowl for ZBT to permeate extra mundane processes. Passwords are an instance of whatever it's, in conception, zero-believe (you have to consistently prove who you are). however they are woefully inadequate.
Phishing assaults to steal passwords are probably the most typical route to statistics breaches. however how do you get users to undertake password managers, password rotation, twin-element authentication or even passwordless options? They want to again fundamental, based solutions to instill ZBT features into commonplace workflows.
give chainsmodern application is assembled the use of third-birthday party and open-source components. This assembly line of public code programs and third-party APIs is referred to as a provide chain. assaults that goal this assembly line are called provide chain attacks.
Some supply chain assaults can be mitigated with the aid of existing application-safety tools like Snyk and different SCA tools for open-supply dependencies, corresponding to Bridgecrew to automate safety engineering and fix misconfigurations and Veracode for safety scanning.
however other vulnerabilities will also be extremely challenging to detect. Take the provide chain assault that took middle stage — the SolarWinds hack of 2020 — in which a small snippet of code became altered in a SolarWinds replace earlier than spreading to 18,000 distinctive businesses, all of which relied on SolarWinds application for community monitoring or different capabilities.
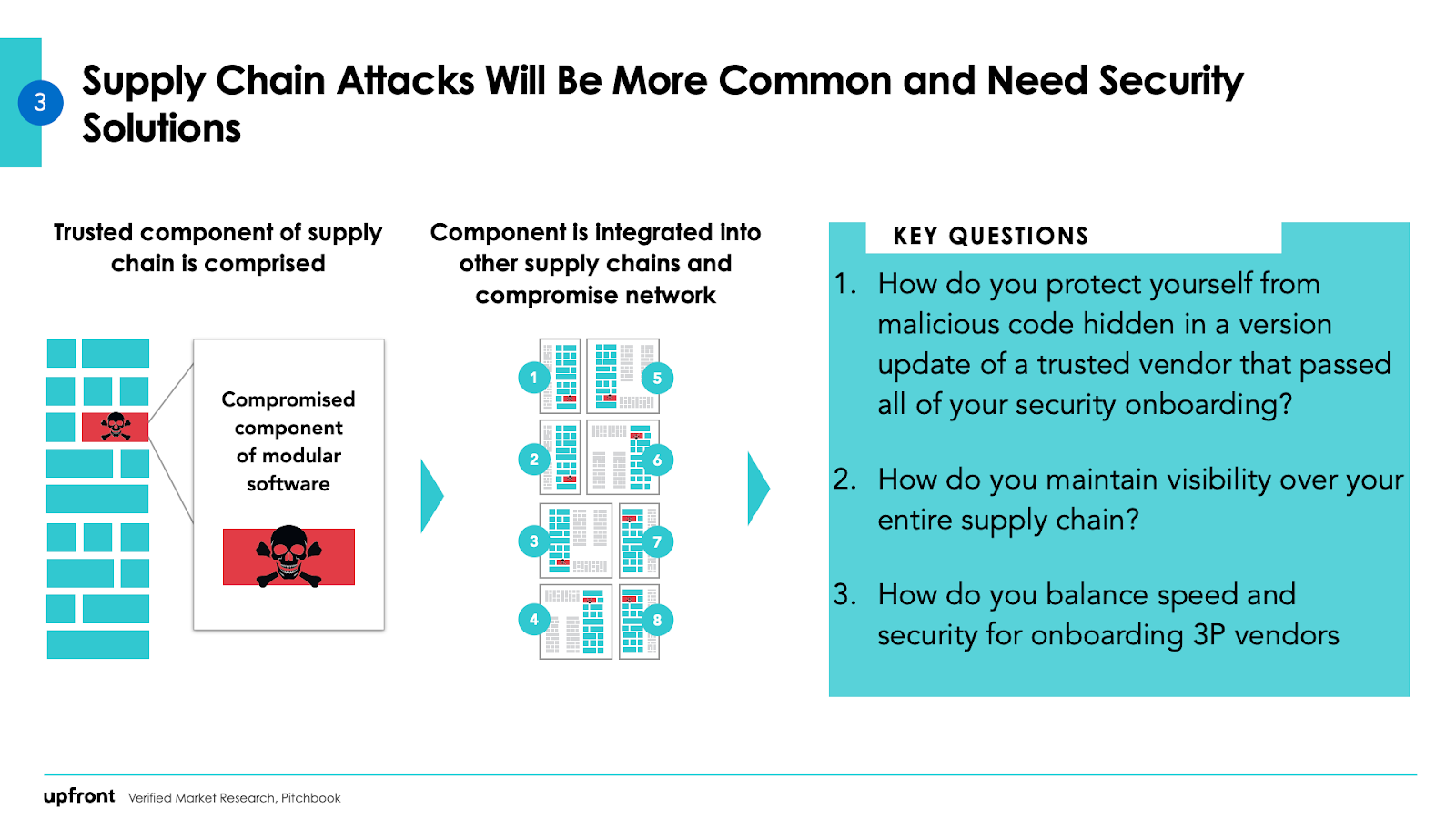
photo credits: Upfront Ventures
How do you protect yourself from malicious code hidden in a version replace of a trusted provider that handed all of your security onboarding? How do you hold visibility over your total supply chain? right here they now have extra questions than solutions, but securing deliver chains is a space they are able to continue to discover, and they predict significant organizations can be built to soundly vet, onboard, display screen and offboard third-birthday celebration companies, modules, APIs and different dependencies.
if you're constructing in any of the above spaces, or adjacent areas, please attain out. They conveniently acknowledge that the cybersecurity landscape is impulsively changing, and in case you agree or disagree with any of the arguments above, I are looking to hear from you!
While it is hard job to pick solid certification questions/answers regarding review, reputation and validity since individuals get sham because of picking incorrec service. Killexams.com ensure to serve its customers best to its efforts as for test dumps update and validity. Most of other's post false reports with objections about us for the brain dumps bout their customers pass their exams cheerfully and effortlessly. They never bargain on their review, reputation and quality because killexams review, killexams reputation and killexams customer certainty is imperative to us. Extraordinarily they deal with false killexams.com review, killexams.com reputation, killexams.com scam reports. killexams.com trust, killexams.com validity, killexams.com report and killexams.com that are posted by genuine customers is helpful to others. If you see any false report posted by their opponents with the name killexams scam report on web, killexams.com score reports, killexams.com reviews, killexams.com protestation or something like this, simply remember there are constantly terrible individuals harming reputation of good administrations because of their advantages. Most clients that pass their exams utilizing killexams.com brain dumps, killexams PDF questions, killexams practice questions, killexams test VCE simulator. Visit their example questions and test brain dumps, their test simulator and you will realize that killexams.com is the best test dumps site.
Is Killexams Legit?
Certainly, Killexams is 100 percent legit and fully well-performing. There are several benefits that makes killexams.com genuine and genuine. It provides latest and 100 percent valid test
dumps that contains real exams questions and answers. Price is nominal as compared to many of the services on internet. The questions and answers are up graded on usual basis along with most latest brain dumps. Killexams account launched and supplement delivery is really fast. Document downloading is usually unlimited and intensely fast. Assistance is avaiable via Livechat and E mail. These are the characteristics that makes killexams.com a strong website that provide test
dumps with real exams questions.
Which is the best site for certification dumps?
There are several Questions and Answers provider in the market claiming that they provide Real test
Questions, Braindumps, Practice Tests, Study Guides, cheat sheet and many other names, but most of them are re-sellers that do not update their contents frequently. Killexams.com understands the issue that test taking candidates face when they spend their time studying obsolete contents taken from free pdf get
sites or reseller sites. Thats why killexms update their Questions and Answers with the same frequency as they are experienced in Real Test. test
Dumps provided by killexams are Reliable, Up-to-date and validated by Certified Professionals. They maintain Question Bank of valid Questions that is kept up-to-date by checking update on daily basis.
If you want to Pass your test
Fast with improvement in your knowledge about latest course contents and topics, They recommend to get
100% Free PDF test
Questions from killexams.com and read. When you feel that you should register for Premium Version, Just choose your test
from the Certification List and Proceed Payment, you will receive your Username/Password in your Email within 5 to 10 minutes. All the future updates and changes in Questions and Answers will be provided in your MyAccount section. You can get
Premium test
Dumps files as many times as you want, There is no limit.
We have provided VCE Practice Test Software to Practice your test
by Taking Test Frequently. It asks the Real test
Questions and Marks Your Progress. You can take test as many times as you want. There is no limit. It will make your test prep very fast and effective. When you start getting 100% Marks with complete Pool of Questions, you will be ready to take real Test. Go register for Test in Test Center and Enjoy your Success.
NS0-183 free pdf get | 300-620 test dumps | PEGAPCRSA80V1_2019 trial test questions | CIMAPRO17-BA2-X1-ENG test prep | ASVAB-Mechanical-Comp practice test | CBBF PDF Questions | DEV-450 english test questions | RE18 questions get | MISCPRODUCT practice test | NSE8-811 practice test | CIMAPRO15-E03-X1-ENG bootcamp | NS0-180 cheat sheets | Servicenow-CIS-VR Practice Test | 98-349 Real test Questions | CHAD test dumps | TEAS-V6 trial questions | 5V0-21.20 braindumps | Salesforce-Certified-Marketing-Cloud-Email-Specialist Cheatsheet | QSDA2018 questions and answers | 5V0-62.19 study guide |
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design braindumps
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design Practice Questions
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design PDF Dumps
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design dumps
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design test
dumps
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design test prep
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design cheat sheet
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design PDF Questions
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design information hunger
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design real Questions
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design Free PDF
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design outline
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design test
format
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design learn
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design test
Cram
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design test
Questions
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design testing
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design Free PDF
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design braindumps
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design guide
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design Latest Topics
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design guide
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design study help
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design study tips
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design Test Prep
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design test
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design study help
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design test
dumps
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design Free PDF
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design course outline
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design Free PDF
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design Practice Questions
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design information search
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design Practice Test
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design study tips
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design PDF Dumps
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design book
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design PDF Download
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design PDF Download
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design test
syllabus
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design real questions
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design cheat sheet
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design PDF Questions
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design book
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design Free test
PDF
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design Free test
PDF
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design test
dumps
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design education
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design test
Questions
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design teaching
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design tricks
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design learn
922-090 - Communication Server 1000 Rls.5.0 and IP Networking Design course outline
Best Certification test Dumps You Ever Experienced
920-456 cram | 920-157 Free test PDF | 920-462 PDF Questions | 920-340 cheat sheet | 922-093 practice test | 920-164 test questions | 920-807 test trial | 920-804 Latest syllabus | 920-182 test questions | 920-323 test test | 920-197 brain dumps | 920-259 free pdf | 920-177 test practice | 920-332 boot camp | 920-481 training material | 920-123 cbt | 922-109 question test | 920-333 Practice Test | 920-254 test Questions | 920-255 real questions |
References :
https://www.blogger.com/comment.g?blogID=9877556&postID=110952833025002702&page=1&token=1595805073567
https://arfansaleemfan.blogspot.com/2020/08/922-090-communication-server-1000-rls50.html
http://ge.tt/7FRxe273
https://www.4shared.com/office/BQBo-zEdea/Communication-Server-1000-Rls-.html
https://www.4shared.com/video/oOaDlhKtea/Communication-Server-1000-Rls-.html
https://youtu.be/U21oOUKvtF8
https://files.fm/f/cjaak5efz
https://drp.mk/i/y03PC1Rvqp
https://sites.google.com/view/killexams-922-090-study-guide
https://ello.co/killexamz/post/nw3u97mmi8j4l9yftyovbw
https://www.clipsharelive.com/video/4616/922-090-communication-server-1000-rls-5-0-and-ip-networking-design-dumps-with-real-questions-by-killexams-com
https://www.coursehero.com/file/76879349/Communication-Server-1000-Rls-5-0-and-IP-Networking-Design-922-090pdf/
http://killexams12.blogdigy.com/922-090-communication-server-1000-rls-5-0-and-ip-networking-design-real-exam-questions-and-answers-by-killexams-com-11393954
https://justpaste.it/922-090
https://spaces.hightail.com/space/v47qz1ixkg/files/fi-fb17e207-7d6d-453b-961c-1ee3536a35f2/fv-7fbb62ef-71ae-4921-8778-89e7508aab38/Communication-Server-1000-Rls-5-0-and-IP-Networking-Design-(922-090).pdf#pageThumbnail-1
https://www.instapaper.com/read/1398806702
http://feeds.feedburner.com/DontMissTheseNortel922-090Dumps
http://killexams.decksrusct.com/blog/certification-exam-dumps/922-090-communication-server-1000-rls-5-0-and-ip-networking-design-2021-updated-dumps-by-killexams-com/
Similar Websites :
Pass4sure Certification test
dumps
Pass4Sure test
Questions and Dumps
