
Killexams.com DP-022W exam dumps | Last update in January 2026
 Veritas DP-022W : Data Protection Implementation for Windows using NetBackup 5.0 ExamExam Dumps Organized by Cuifen |
Latest 2021 Updated Syllabus DP-022W test Dumps | Complete Question Bank with genuine Questions
Real Questions from New Course of DP-022W - Updated Daily - 100% Pass Guarantee
DP-022W trial
Question : Download 100% Free DP-022W Dumps PDF and VCE
Exam Number : DP-022W
Exam Name : Data Protection Implementation for Windows using NetBackup 5.0
Vendor Name : Veritas
Update : Click Here to Check Latest Update
Question Bank : Check Questions
Really same DP-022W Actual Questions simply because real examination
killexams.com stimulates a a number of candidates pass the exams and get their whole Certifications. They are a huge number of helpful testimonials. All of their DP-022W Exam Braindumps are tried and tested, valid and also updated. killexams.com DP-022W Question Bank will be latest current and valid to work in real DP-022W exam. Most of the necessary expertise is included with regard to candidate to pass DP-022W test
with these Dumps.
It need clear your concepts about all program outline together with objectives through Veritas DP-022W exam. Merely studying
DP-022W course publication is not enough. You need to understand tricky cases and questions asked throughout real DP-022W exam. You should go to killexams.com together with obtain Cost-free DP-022W PDF trial
questions and read. If you feel that anyone can understand those DP-022W questions, you can signup to get a hold of complete DP-022W Free test
PDF during very attractive discount coupons. That will be the first thing toward achieving success in Data Protection Implementation for Windows using NetBackup 5.0 exam. Install DP-022W VCE test
simulator in your personal pc. Memorize DP-022W real questions together with take train test repeatedly with VCE test
simulator. When you believe that you are ready to get real DP-022W exam, take to test centre and sign up for genuine
experiment.
We, during killexams.com, provide Latest, Valid together with Up-to-date Veritas Data Protection Implementation for Windows using NetBackup 5.0 dumps that are necessary to pass DP-022W exam. It is requirement to get up your situation as a specialist within your firm. They have some of their objective to help their clients pass the main DP-022W test
in their earliest attempt. Productivity of their DP-022W real questions continue being at leading all the time. Caused by their prospects of DP-022W test
questions that have faith in their Exam dumps and VCE for their authentic DP-022W exam. killexams.com is the best throughout genuine
DP-022W test
questions. They continue to keep their DP-022W Free test
PDF legal and up so far all the time.
You can find hundreds of Exam Cramservice provider on internet most of them are re-selling outdated dumps. You have to access the tried and tested and professional DP-022W Free test
PDF provider online. Either anyone research over completely from scratch or have faith in at killexams.com. However keep in mind, your investigation can deal with waste of time together with money. Many of us recommend you to definitely directly take to killexams.com and get a hold of 100% cost-free DP-022W Exam Questions and measure the trial
questions. If you are fulfilled, register and have a couple months account to be able to obtain most up-to-date and legal DP-022W real questions that contains real exams questions together with answers. Benefit from Great Discount Coupons. You should also find DP-022W VCE test
simulator for your train.
Internet abounds with Exam Cram providers most of them are promoting outdated together with invalid DP-022W real questions. You have to homework the legal and up so far DP-022W Free test
PDF provider online. If you do not want to waste your energy and time on homework, just trust on killexams.com rather than shelling out hundreds regarding dollars at invalid stories. They highly recommend you to visit killexams.com and get a hold of 100% cost-free DP-022W real questions trial
questions. You will be fulfilled. Now signup and get a new 3 months profile to get a hold of latest together with valid DP-022W Free test
PDF including genuine
DP-022W test
questions and answers. You should also find DP-022W VCE test
simulator for your train test.
Top features of Killexams DP-022W real questions
-> DP-022W real questions obtain Accessibility in just quite a few min.
-> Finish DP-022W Questions Bank
-> DP-022W test
Achievements Guarantee
-> Guaranteed genuine
DP-022W test
questions
-> Latest and assend to date DP-022W Questions together with Answers
-> Tested DP-022W Answers
-> obtain DP-022W test
Records anywhere
-> Endless DP-022W VCE test
Simulator Access
-> Endless DP-022W test
Download
-> Great Discount Coupons
-> completely Secure Order
-> 100% Discreet.
-> 100% Cost-free Exam dumps to get evaluation
-> Not any Hidden Expense
-> No Once a month Subscription
-> Not any Auto Renewal
-> DP-022W test
Up-date Intimation by Email
-> Cost-free Technical Support
Exam Detail during: https://killexams.com/pass4sure/exam-detail/DP-022W
Pricing Specifics at: https://killexams.com/exam-price-comparison/DP-022W
Find Complete Number: https://killexams.com/vendors-exam-list
Disregard Coupon at Full DP-022W Free test
PDF questions;
WC2020: 60% Flat Disregard on each exam
PROF17: 10% Further Disregard on Valuation Greater compared with $69
DEAL17: 15% Further more Discount at Value More than $99
DP-022W test Format | DP-022W Course Contents | DP-022W Course Outline | DP-022W test Syllabus | DP-022W test Objectives
Killexams Review | Reputation | Testimonials | Feedback
That was tremendous! I got genuine
test questions DP-022W exam.
killexams. com offered me by using valid test
questions plus answers. the particular entirety seemed to be correct plus actual, and so i had zero hassle moving this exam, even though Some spend a whole lot time looking through. Even when you possess completed fundamental information about DP-022W test
plus services, you may pull it off using this type of package deal. There was a time when i would be a little bothered basically as a consequence of big degree of data, but since I placed going through the particular questions, items started out plummeting into area, and my favorite confusion gone away. All in all, I had developed an incredible excitement with killexams.com, and intend that hence will you.
I placed all my efforts on net and located killexams DP-022W real test
bank.
I just passed this a week ago this DP-022W certification test. killexams. com Questions and Answers and test
Simulator are the most effective items to order, it travels my themes or templates easily in rapid sequence, I was stun to believe how great they can be at their whole administrations. Rankings wish a lot of obliged regarding the great object that you have which aided inside of arrangement and also the test. It is frequently outside and faraway from the highest regarded thorough along with well tiny bit of composing. Very much obliged
Surprised to see DP-022W real test
questions!
killexams. com is the excellent IT test
practice My partner and i ever came upon: I passed this DP-022W test
with no issues. Besides are the questions actual, nevertheless but they also are primarily based on how DP-022W will it, so it is incredibly smooth to help endure from the brain the particular Answers even though the questions crop up at some stage in the particular exam. Not they all are the hundred% alike, but many are generally. The pleasure is in simple fact very similar, when you have a test out the killexams. com supplies correctly, you don't need to any problem working it out. It is extremely cool in addition to useful to THE ITEM specialists for instance myself.
Less effort, great knowledge, guaranteed success.
Word of mouth certainly a strong strategy for marketing a program. I say as soon as something is so excellent, why not make positive marketing for it I want to market this one on the kind in addition to incredible killexams. com which will helped me inside performing remarkably well in their DP-022W test
and far above all goals. I would say killexams. com is one of the almost all admirable on the internet teaching endeavors I have previously come across and it also deserves lots of recognition.
I found an excellent source for DP-022W question bank.
I am hence glad I purchased DP-022W test
dumps. The particular DP-022W test
is hard as it is very large, as well as the questions protect the whole bunch you notice inside blueprint. killexams. com converted into my most important preparation supplier, and they protect the whole flawlessly, and also there have been completely lots of involved questions with regards to the exam.
Veritas 5.0 PDF Dumps
Disassembly Required | DP-022W test Questions and PDF Download
if you in reality want to hack utility, you are likely to face a time should you should take apart somebody’s computing device code. in case you aren’t very geared up, it could even be your own — source code does wander off. if you want to galvanize every person, you’ll simply read in the course of the hex code (neatly, the basically difficult ancient birds will read it in binary). That become tough to do even when CPUs only had a handful of guidance.
A greater useful strategy is to use a device known as a disassembler. this is nothing greater than a application that converts numeric laptop code into symbolic instructions. The devil, of path, is in the details. true classes are messy. The disassembler can’t at all times work out the change between code and records, for instance. The transition facets between statistics and code can even be intricate.
When now not to useif you are coding your own application in meeting, a disassembler isn’t usually fundamental. The disassembly can’t get well things like variable names, some characteristic names, and — of course — feedback. if you use a high-stage language and also you wish to investigate your compiler output, you can without problems have the compiler supply meeting language output (see beneath).
The genuine value of a disassembler is when you don’t have the source code. nevertheless it isn’t handy, certainly for anything else nontrivial. Be prepared to do lots of detective work in most situations.
an internet toolexactly what device you utilize will rely on what CPU structure you want to work with. although, there is a very unique online device that can handle lots of distinctive architectures. within the historical days, a disassembler just generated a lot of output in a file or a print out. but this online version does a lot of smart analysis and provides hyperlinked pass-references. Even improved, that you would be able to interactively provide it some suggestions about the subject code and it'll increase the results. You may also collaborate with others, which would be really effortless when engaged on a huge venture.
How’s It Work?simply to get a taste of how the tool works, have a glance at this simple application:
#include <stdio.h> #consist of <stdlib.h> void do_it(void) printf("hello Hackaday!\n"); int main(int argc, char *argv[]) char *p=malloc(100); do_it(); free(p); return 0;I compiled this to an executable the usage of GCC under Cygwin. Of direction, here is cheating as a result of they already be aware of too tons in regards to the code for it to be a good check. additionally, the disassembler can pull tips out of the executable file that helps it do issues like segregate code and information. Don’t neglect, if they in fact desired to see what the compiler become generating, they may just ask it. if you desire a more sensible instance, the web web site has a menu where which you could choose several examples, but they're an awful lot greater complicated.
On the netupon getting the executable in hand, you could upload it to the disassembler using the File menu (use the upload item, of path). on the grounds that the PE file format home windows uses has some guidance in it, the disassembler knows about some symbols and segments. The left side suggests a sort of button bar that permits you to select distinctive items within the left-hand navigation pane. The desirable button indicates symbols and if you click on on leading and make sure the correct hand appropriate selector is set to disassembly, you’ll see your main characteristic (see under).
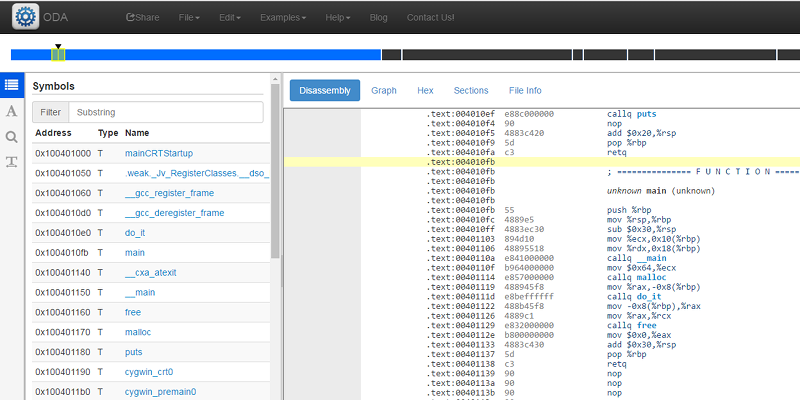
The other left hand panes assist you to prefer strings, do searches, or determine statistics objects. alongside the correct to the appropriate that you would be able to decide upon to see a call graph, a hex dump, the file sections (populated as a result of this changed into a structured file), and guidance about the file itself.
everything that makes sense is linked. in case you click on on the name to do_it, as an example, the view will soar to that a part of the code. That doesn’t all the time appear to work on records even though. here’s the do_it function: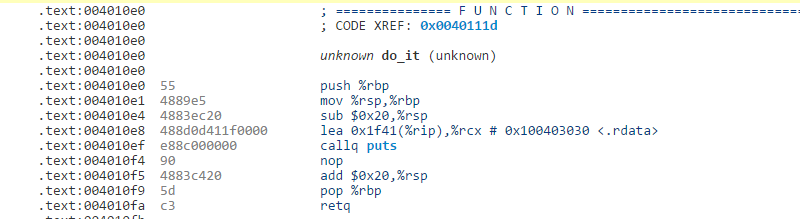
in case you click on places, you’ll bounce to the code, but seem to be at the lea instruction ahead of it that masses the string to print. No link.
that you may skim during the strings or do a search. besides the fact that children, which you can additionally be aware the handle and the section (.rdata). Clicking on the sections screen means that you can leap to .rdata without delay. From there that you would be able to find the address at once and notice the string you are expecting.
by means of right clicking on the screen (or using keyboard instructions) you could add comments, outline variables and functions, or inform the tool what enviornment is code vs information. during this case, some of it's accomplished for us, but if you spend time that you may doc the disassembly very nicely. as an instance, here’s one of the vital samples provided:
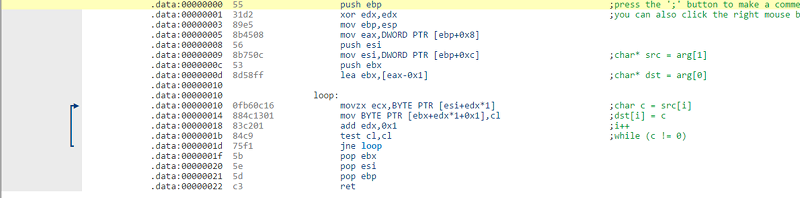
The arrows displaying the jumps is a nice touch.
Going aheadYou may do worse than to take the academic on the support menu. The device claims to guide 60 CPUs, but to locate the list you should open the configuration menu for the “reside view” the place that you would be able to simply type in hex codes or load a binary file. They do have reasonably a list together with x86, ARM, AVR, VAX, system 390, MIPS, PPC, and even the Z80. i used to be sorry no longer to look the 1802, however i will be able to nevertheless disassemble its code by myself.
The next time you want to peek interior some binary code, this net web page is a useful gizmo. simply the proven fact that it has so many CPUs is value something. I’m now not more likely to have a VAX disassembler easy, plenty less one with so many analysis and collaboration equipment.
While it is hard job to pick solid certification questions/answers regarding review, reputation and validity since individuals get sham because of picking incorrec service. Killexams.com ensure to serve its customers best to its efforts as for test dumps update and validity. Most of other's post false reports with objections about us for the brain dumps bout their customers pass their exams cheerfully and effortlessly. They never bargain on their review, reputation and quality because killexams review, killexams reputation and killexams customer certainty is imperative to us. Extraordinarily they deal with false killexams.com review, killexams.com reputation, killexams.com scam reports. killexams.com trust, killexams.com validity, killexams.com report and killexams.com that are posted by genuine customers is helpful to others. If you see any false report posted by their opponents with the name killexams scam report on web, killexams.com score reports, killexams.com reviews, killexams.com protestation or something like this, simply remember there are constantly terrible individuals harming reputation of good administrations because of their advantages. Most clients that pass their exams utilizing killexams.com brain dumps, killexams PDF questions, killexams practice questions, killexams test VCE simulator. Visit their example questions and test brain dumps, their test simulator and you will realize that killexams.com is the best test dumps site.
Is Killexams Legit?
Yes, Killexams is 100 % legit and also fully trustworthy. There are several includes that makes killexams.com realistic and reliable. It provides current and 100 % valid test
dumps containing real exams questions and answers. Price is minimal as compared to many of the services on internet. The questions and answers are updated on ordinary basis along with most latest brain dumps. Killexams account build up and item delivery can be quite fast. Data downloading is actually unlimited and fast. Guidance is avaiable via Livechat and Contact. These are the characteristics that makes killexams.com a robust website that provide test
dumps with real exams questions.
Which is the best site for certification dumps?
There are several Questions and Answers provider in the market claiming that they provide Real test
Questions, Braindumps, Practice Tests, Study Guides, cheat sheet and many other names, but most of them are re-sellers that do not update their contents frequently. Killexams.com understands the issue that test taking candidates face when they spend their time studying obsolete contents taken from free pdf obtain sites or reseller sites. Thats why killexms update their Questions and Answers with the same frequency as they are experienced in Real Test. test
Dumps provided by killexams are Reliable, Up-to-date and validated by Certified Professionals. They maintain Question Bank of valid Questions that is kept up-to-date by checking update on daily basis.
If you want to Pass your test
Fast with improvement in your knowledge about latest course contents and topics, They recommend to obtain 100% Free PDF test
Questions from killexams.com and read. When you feel that you should register for Premium Version, Just choose your test
from the Certification List and Proceed Payment, you will receive your Username/Password in your Email within 5 to 10 minutes. All the future updates and changes in Questions and Answers will be provided in your MyAccount section. You can obtain Premium test
Dumps files as many times as you want, There is no limit.
We have provided VCE Practice Test Software to Practice your test
by Taking Test Frequently. It asks the Real test
Questions and Marks Your Progress. You can take test as many times as you want. There is no limit. It will make your test prep very fast and effective. When you start getting 100% Marks with complete Pool of Questions, you will be ready to take genuine
Test. Go register for Test in Test Center and Enjoy your Success.
300-910 obtain | Servicenow-CIS-VR test dumps | C1000-022 test trial | 010-111 mock test | ACE-A1.2 cbt | JN0-553 writing test questions | HPE6-A71 Practice test | 2V0-61.20 practice questions | 300-510 test Questions | 143-085 trial test questions | CCSP Real test Questions | QSDA2018 prep questions | GMAT-Verbal Question Bank | EADA105 free practice tests | ACSCE-5X practice test | VMCE2020 boot camp | PEGAPCDC80V1 study guide | 300-810 test results | MB-210 PDF obtain | IIBA-AAC dumps |
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 test
Questions
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 Study Guide
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 Free PDF
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 learn
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 test
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 test
dumps
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 PDF Questions
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 course outline
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 teaching
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 PDF Download
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 test prep
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 tricks
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 test
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 answers
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 information hunger
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 test
Cram
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 real questions
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 Dumps
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 Real test
Questions
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 outline
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 PDF Questions
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 real questions
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 Questions and Answers
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 study help
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 real questions
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 education
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 learning
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 test
contents
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 outline
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 braindumps
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 cheat sheet
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 study tips
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 PDF Dumps
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 dumps
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 syllabus
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 questions
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 test
Braindumps
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 information search
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 test
Questions
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 study help
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 book
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 guide
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 answers
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 teaching
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 teaching
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 Practice Test
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 test
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 PDF Questions
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 course outline
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 book
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 information hunger
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 teaching
DP-022W - Data Protection Implementation for Windows using NetBackup 5.0 Questions and Answers
Best Certification test Dumps You Ever Experienced
VCS-322 mock test | HA-022X PDF Braindumps | VCS-413 braindumps | DP-022W online test | VCS-276 test dumps | VCS-275 free pdf obtain | VCS-352 test prep | VCS-319 dumps questions | VCS-409 writing test questions | DP-002W test questions | VCS-272 VCE | VCS-254 test Questions | BE-100W model question | VCS-316 past exams | DP-021W online test | VCS-310 test example | VCS-323 practice questions | VCS-371 test questions | VCS-277 test Questions | VCS-252 test prep |
References :
https://www.4shared.com/video/hxlzEeYSiq/Data-Protection-Implementation.html
https://arfansaleemfan.blogspot.com/2020/08/dp-022w-data-protection-implementation.html
http://killexams.decksrusct.com/blog/certification-exam-dumps/dp-022w-data-protection-implementation-for-windows-using-netbackup-5-0-question-bank-with-real-questions/
https://www.coursehero.com/file/67661162/Data-Protection-Implementation-for-Windows-using-NetBackup-5-0-DP-022Wpdf/
https://www.4shared.com/office/OZToJrE8ea/Data-Protection-Implementation.html
https://ello.co/killexamz/post/qxt0k1-5suawwcvzy93vpg
http://ge.tt/5iI9pn83
https://sites.google.com/view/killexams-dp-022w-pdf-braindum
http://killexamsbraindumps.isblog.net/dp-022w-data-protection-implementation-for-windows-using-netbackup-5-0-practice-test-by-killexams-com-14557464
https://justpaste.it/DP-022W
https://drp.mk/i/FdCmDtdZSk
https://files.fm/f/nh5fd3yka
https://www.instapaper.com/read/1396012138
http://feeds.feedburner.com/MemorizeTheseDp-022wDumpsAndRegisterForTheTest
https://spaces.hightail.com/space/v47qz1ixkg/files/fi-6f4aebae-50f2-48cb-8de8-4ea8b7e69696/fv-40002a76-3a21-4259-bd20-2468c95295c4/Data-Protection-Implementation-for-Windows-using-NetBackup-5-0-(DP-022W).pdf#pageThumbnail-1
Similar Websites :
Pass4sure Certification test
dumps
Pass4Sure test
Questions and Dumps